Bitcoin on the iNGENIOUS Platform
By POLISH-JAPANESE ACADEMY OF INFORMATION TECHNOLOGY

Let’s start with a little bit of history. During the financial crisis of 2008 the trust in financial institutions, especially banks, and the governments eroded. The idea to opt-out of the traditional monetary system based on faith in central banks gained traction. Many ideas were tried. Most of them failed. For example, the initiative to establish Liberty Dollar, a currency that would be based on equities such as gold, was thwarted by the Fed. It turned out that it can be easily done if there is an identifiable entity responsible for operation. So, any alternative solution should avoid one central point of failure.

The solution to this problem was provided by pseudonymous author Satoshi Nakamoto in a 9-page long manifesto “Bitcoin: Peer-to-peer electronic cash system” . The idea behind bitcoin is to use proof-of-work to establish consensus on the state of the whole transaction ledger by means of a distributed method. To minimize attack surface of Bitcoin, including social attacks, the principles on which the bitcoin platform operates are hardwired into algorithms of the protocol. Any substantial change requires consensus among Bitcoin users.

Bitcoin as a currency (BTC). The supply of Bitcoin tokens is limited to 21M, and it takes computational effort to discover new ones. Each Bitcoin is divided into 100M satoshis. At first it had no value and circulated feely among cypherpunks. The first real-world usage was to buy a pizza from Papa Johns for 10 000 BTC, and since then the value of Bitcoin goes up, in general. The interesting property of Bitcoin network is that it is more secure, when the native token is more expensive.
Bitcoin does not require registration to use – transactions are generated on the local computer of the user.
Users don’t need to ask anybody to do anything to perform a transaction. Thus, the platform allows unlimited and uncontrolled access to digital financial services.
Bitcoin transactions are irreversible, so merchants don’t have to worry about chargebacks.

The supply schedule of BTC is driven by the code (in contrast to traditional currencies). This leads to high volatility of Bitcoin with respect to major currencies. On the other hand it offers certainty about monetary policy. This is, because it is impossible for program to determine the value of real-world things.
Bitcoin supports confidentiality, because the access to funds is based on public key cryptography, and the keys can be recovered using mnemonic seed that is just a sequence of words.
All the above was made possible by advances in cryptography, in areas such as digital signatures, hashing algorithms, p2p networks. In particular, the problem of double spending in a distributed system without central authority that would finalize transactions – an instance of Byzantine Generals Problem – was solved by Bitcoin.
Now let’s move to more technical details. Bitcoin network works in a peer-to-peer fashion. There are no accounts, only transactions. Transactions represents transition of funds. Each transaction has inputs and outputs. The outputs are protected by the digital signatures. In fact, the signature takes the form of a „script” – formula in reverse Polish notation with one missing part. That missing part is the key to unlock the funds. Those transactions that have not yet spent their outputs are handled in so called UTXO set and represents the current state of the balances on the network. Every full node in Bitcoin network holds the whole history of transactions.
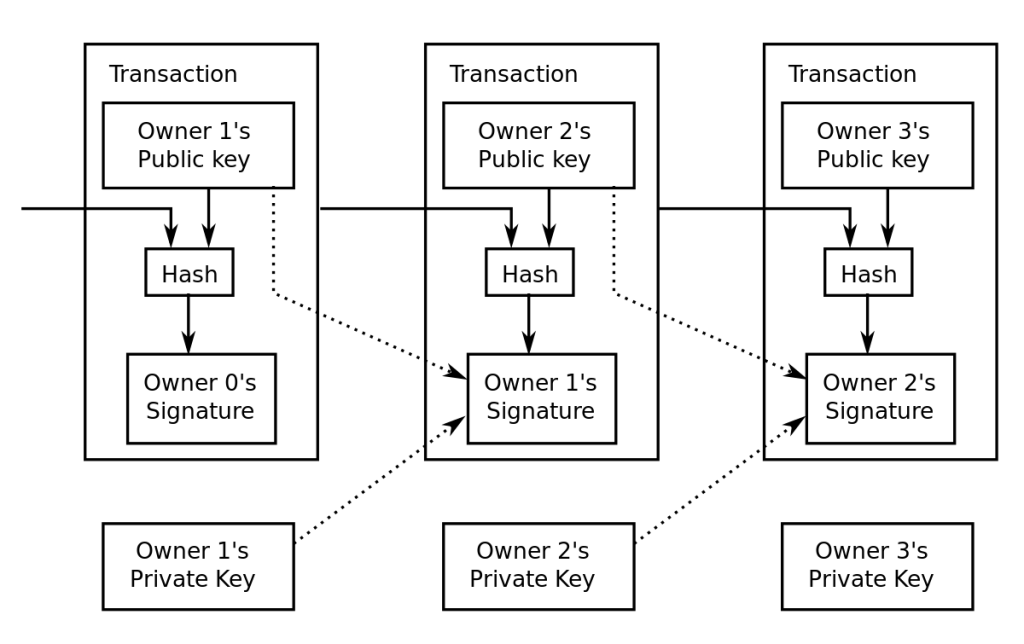
The transactions are grouped in blocks and organized in a chain of blocks; a data structure nowadays called blockchain. Each block includes cryptographic hash of the previous block. The only block that is the exception is the genesis block, the first block of the blockchain. This block (or its hash) is hard-coded in the software. In order to change some old transaction, one has to recalculate hashes on each block since the block containing altered transaction. The hash link between blocks provides this feature. The most significant part is the way to achieve consensus. Bitcoin networks is distributed system, so it does not have one central authority that decides which blocks are valid and prevent forks in the blockchain. The solution is to resort to the proof-of-work idea, with difficulty adjustment to make the process of Bitcoins discovery last longer. The process, called mining, can be compared to brute-force recovery of a password from its hash. Technically speaking, the hash of valid block must be less than a given threshold. Thus, the mining process amounts to guessing different parts of a new block so that its hash is smaller than the threshold. The longest proof-of-work chain obtained in this way is treated as the true one.
The base layer of the Bitcoin network, i.e., the basic operations of Bitcoin, has some limitations. They are in place, because the main goal of Bitcoin is to be unconfiscatable, uncensorable, permissionless, independent, p2p global digital currency. One of the limitations is the 1MB block size. Every 10 minutes around 1MB of data can be stored by the nodes of the network. It is impossible to increase the frequency of blocks for longer time because difficulty adjustment kicks in and increases difficulty to reach the target of 10 minutes per block. It is extremely inefficient in terms of throughput and cost per MB of data. Yet it allows better decentralization of crucial aspects of Bitcoin. For example, the time between blocks is long enough that every interested miner (the entity that generates blocks) will be in sync with the network regardless of its connection to the Internet quality. The size of blocks is limited, so the cost of storing blockchain is rather low. The scaling of Bitcoin in terms of throughput is performed on so called second layer solutions. One of the examples is Lightning Network, see “The Bitcoin Lightning Network: Scalable Off-Chain Instant Payments” – Joseph Poon, Thaddeus Dryja. Lightning Network is based on the idea of locking Bitcoins on chain in a multi-signature wallet with some additional tricks and performing transactions between participants by updating the unpublished transactions. Roughly speaking, it allows transfer of funds by so-called multihop payments that are atomic and cryptographically protected, so the middleman cannot steal funds. It allows for theoretically no upper limit in transactions per second, but there are some open problems. For example, how to efficiently perform routing of payments in dynamically changing graph of balances. There are many more approaches that leverage the security of the base layer to provide additional usability on the second layer.
From the point of view of iNGENIOUS the most interesting feature of Bitcoin is the immutability of the ledger. Based on the 12-year history of Bitcoin, we can assume that it will continue to operate and provide extremely high level of security in the foreseeable future. We will rely on Bitcoins’s ledger immutability to store the proof of existence of the data. Theoretically, it is possible to change the data stored on Bitcoin’s blockchain, but the cost would be enormous – one would have to recalculate every block since the one that is modified, and also calculate new blocks faster than the rest of the network until the changed fork is accepted. This renders any such attempt infeasible in practice. On the other hand, it is computationally easy to verify that the data have been written to the blockchain.
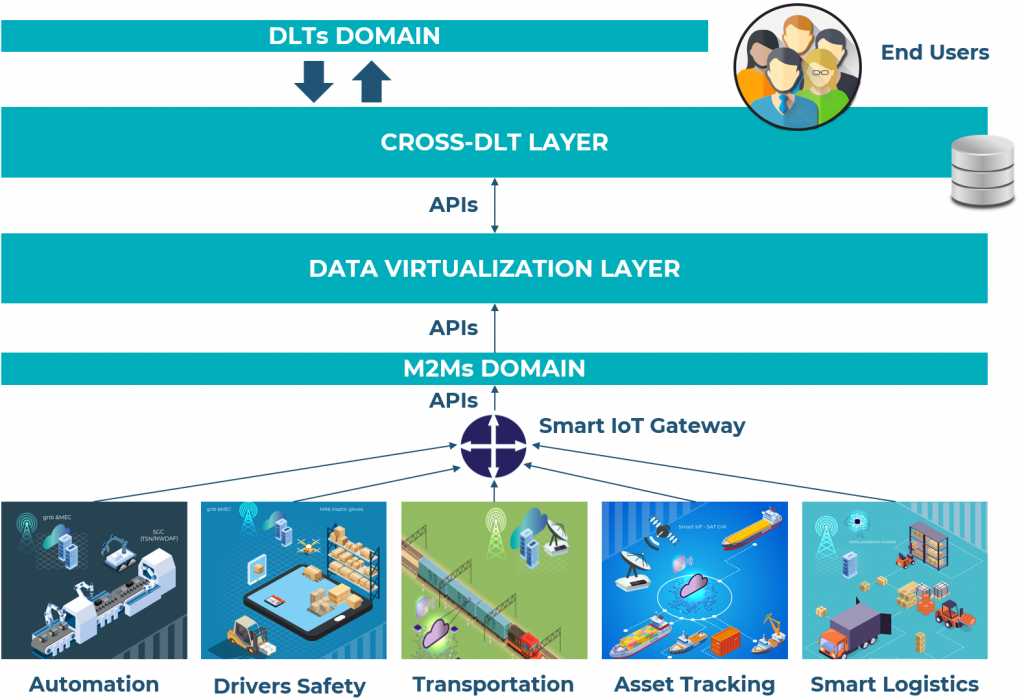
Apart from Bitcoin also other Distributed Ledger Technologies (abbr.: DLT) will be used in the Cross-DLT layer of the iNGENIOUS solution. We believe that this will provide the users the choice of methods and tools needed in today’s world.




