The iNGENIOUS Cross-Layer Architecture
by Barkhausen-Institut

iNGENIOUS is a rather large project and its 21 partners contribute a very diverse set of technologies to build the next-generation supply chain. Accordingly, there are complex interactions and interdependencies between all the technological components. This blog post shall give an overview of iNGENIOUS from the technical side.
The cross-layer architecture is derived from the functional and non-functional requirements that have been identified within the use cases of the project. Each use case will be described in detail in future articles on this blog, but we will briefly summarize them here to motivate the iNGENIOUS overall architecture. There are six use cases in total:

Automated robots with heterogeneous networks 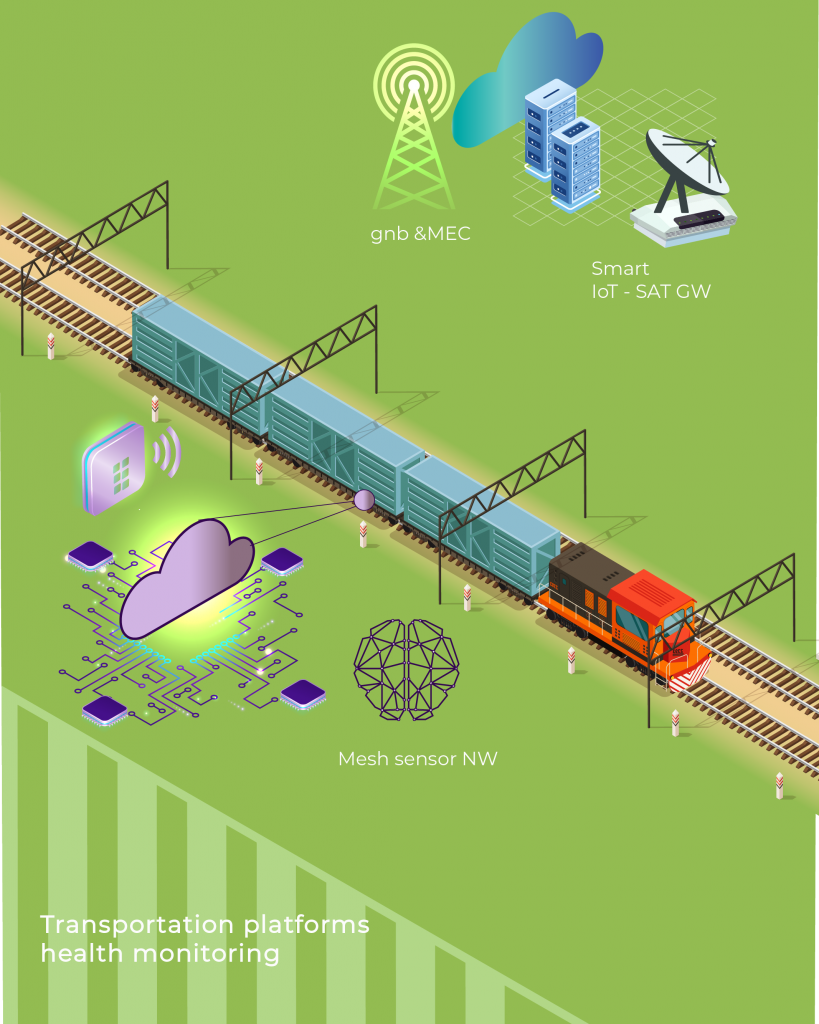
Transportation platform health monitoring 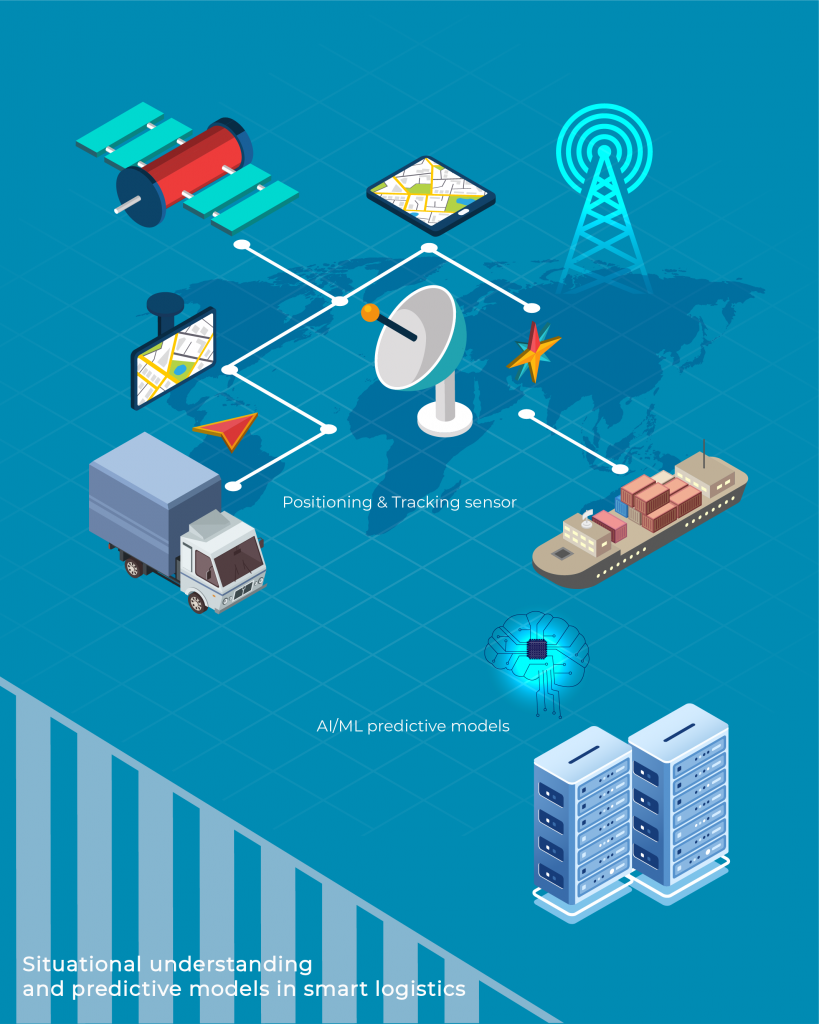
Situational understanding and predictive models in smart logistics scenarios 
Improve drivers’ safety with mixed-reality and haptic solutions 
Inter-modal asset tracking via IoT and satellite technology 
Supply chain ecosystem integration
The principle approach of the iNGENIOUS project and all these use cases is to exploit the wealth of data provided by the Internet of Things (IoT) for the entire supply chain. It starts right in the factories, where automated robots increase efficiency by working fully autonomously or by assisting human workers. To innovate logistics, IoT sensors shall monitor the safety-critical parts of land-based transport vehicles, thereby enabling longer maintenance intervals to reduce costs and ensuring reliable detection of defects that could otherwise lead to accidents. By integrating network technologies ranging from local-area wireless networks all the way up to satellites, the project aims to enable comprehensive tracking of assets in shipping containers across land and sea. INGENIOUS also seeks to develop tools for optimising container loading and unloading in ports, as well as to exploit 5G networks to remotely control vehicles in situations, where humans would be in danger or exposed to adverse environmental conditions. Key to enabling these use cases is the:
- ability to access all the data flows that accompany physical goods through logistics and supply-chain data networks, and
- low-latency and reliable communication between sensors, controllers, and actuators in factory and port scenarios.
The data-access challenge is primarily considered in the last two use cases, but from an architectural point of view, it applies to all of them. The security and privacy requirements associated with comprehensive data access require a system architecture where technologies from many stakeholders are integrated across all layers. The same is true for the time-critical communication links to IoT-enabled machinery like robots, but typically at lower distances to minimize latency. The architecture to support the iNGENIOUS approach must therefore be a true cross-layer architecture.
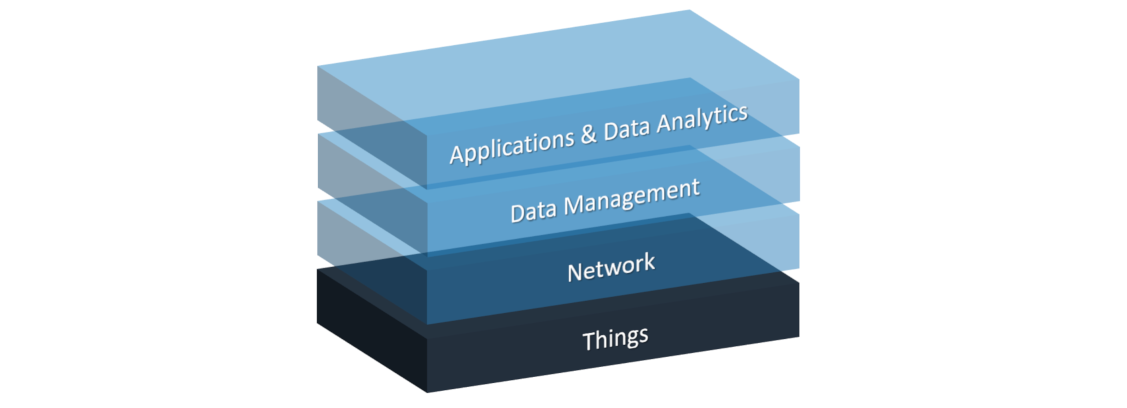
The iNGENIOUS architecture consists of four layers. The first three layers ranging from low-level hardware over heterogeneous networks to data management and analytics services are generic. A fourth layer on top hosts applications and application-specific data analytics that rely on the services provided by iNGENIOUS components underneath.
The “things” layer at the bottom of the iNGENIOUS architecture includes all IoT devices such as sensors and actuators. These devices interact with the physical world and some of them can be moved (e.g., because they are part of a vehicle or attached to a shipping container). Sensors and actuators require embedded computers and network communication hardware to become IoT devices. These components are part of the bottom layer as well and the latter (e.g., wireless modems) are right at the boundary to the network layer.
Most “thing” components are only needed for specific use cases, but representatives of generic classes such as sensors or actuators are always present. The first figure shows an instantiation of the IoT device layer with IoT devices relevant to use cases about driver safety, tracking assets in shipping containers, and situational understanding of smart logistics in the port area.
As IoT devices serve many different and very diverse purposes, there is no one-size-fits-all solution for connecting them to a network. For those that operate in a fixed location, it may be practical to use wired connections. But most of them – especially those needed in logistics scenarios – only make sense with wireless connections. Depending on the device type, energy constraints, and operating environments, different radio technologies need to be used. Hence, the iNGENIOUS architecture must support heterogeneous networks to cover a multi-dimensional space of range, bandwidth, latency, reliability, and energy-efficiency demands. The iNGENIOUS network layer includes 3GPP-compliant networks such as such as Cellular IoT and 5G and non-3GPP networks, some of which are integrated into the architecture via a smart IoT gateway. To support transportation health and container shipping use cases, satellite connectivity is considered and part of the iNGENIOUS network layer as well.
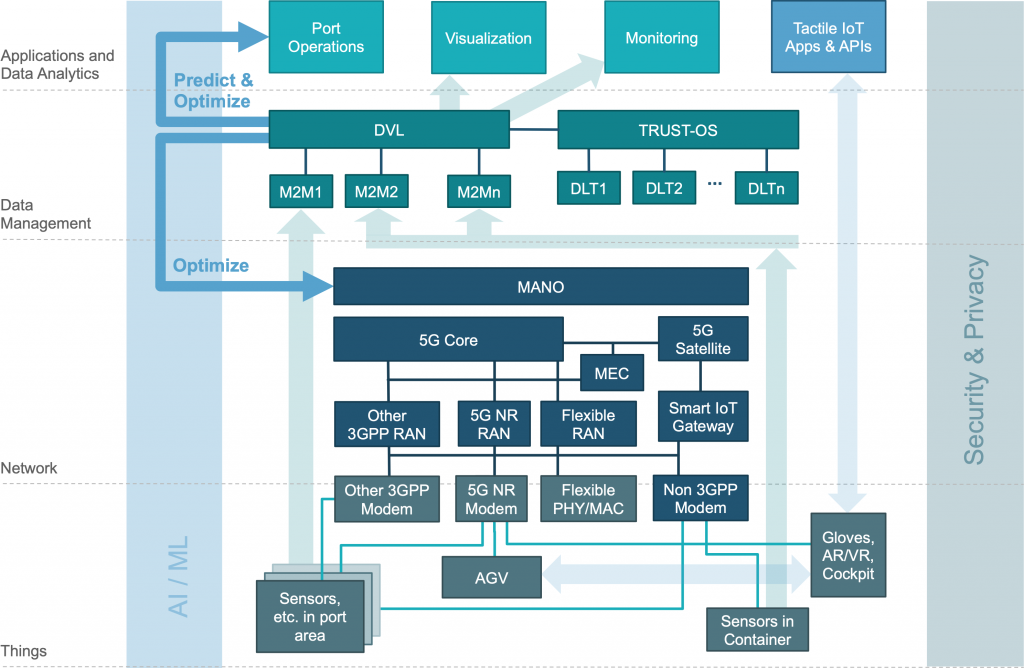
IoT devices not only differ in terms of radio connectivity, but existing data management solutions serving different stakeholders in the supply chain are realised as several, incompatible machine-to-machine (M2M) platforms. The Data Virtualisation Layer (DVL) makes data from all these M2M silos accessible using one common interface, thereby enabling comprehensive end-to-end tracking and monitoring of assets through the supply chain. It is also a critical component needed for predictions and optimisations of logistics operations in the port scenario. The DVL also serves as the central component to ensure the integrity of all supply chain data by logging them in distributed ledger networks. Multiple Distributed Ledger Technology (DLT) systems are supported by the iNGENIOUS architecture; it is the responsibility of the Cross-DLT Layer, implemented by TRUST-OS, to virtualise the DLTs and to record securely all transactions passing through the DVL.
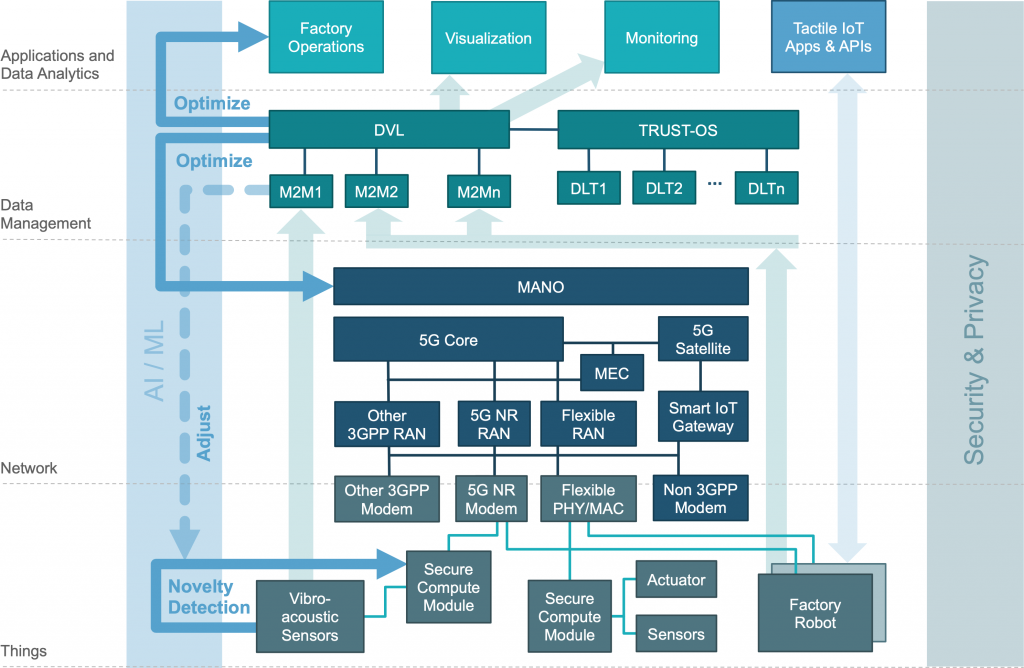
Many of the innovations that iNGENIOUS aims to create are only possible because technologies from multiple layers of the architecture are combined to enable new and powerful cooperation. The first cross-layer concern in the iNGENIOUS architecture is the use of Artificial Intelligence and Machine Learning (AI/ML). For example, at the application level, ML models are trained on data provided by the DVL together with observed arrival times of sea vessels. Later, the same types of data about sailing ships are used to more accurately predict when they will arrive at the port. A similar approach is used at the application level to optimise truck turn-around times in the port. But as a cross-layer technology, AI/ML is also employed to optimise internal iNGENIOUS services, namely within the Management and Network Orchestration (MANO) component of a 5G network so as to adapt assignment of network resources to IoT devices at the “things” layer. In addition to that, ML-based data processing is used at the edge within energy-constrained IoT sensors. ML usage across all layers is shown in another instantiation of the iNGENIOUS architecture in the second picture, which includes vibro-acoustic sensors with neuromorphic processing capabilities; they are used in the transportation-health use case. The AI/ML-related interactions are visualised by the blue arrows on the left-hand side of the above figure.
The second cross-layer aspect of the architecture is about security and privacy. Privacy is one of the key factors to be addressed by iNGENIOUS and the DVL plays an important role on its implementation. It will act as a pseudonymization entity for all the uses cases that need to handle personal data according to GDPR directives. The cooperation between the DVL and the DLTs enables manipulation-proof recording of observed events and thus provides a critical building block to ensure data integrity across the entire supply chain. In the network layer, 5G networks incorporate security enhancements over previous 3GPP standards, from which all use cases benefit. For example, in the factory use case, where robots are remote controlled by smart applications running in a nearby Multi-access Edge Cloud (MEC). Securing the communication links that transmit both sensor readings and actuator commands is essential to guarantee safety of automated factory operations, especially when humans are present as well. The security requirements are similarly obvious when regarding the remotely-operated vehicles in the port use case (see AGV and AR/VR cockpit in the second figure), but they benefit all use cases in the end. Finally, the lowest layer plays a critical role in the iNGENIOUS security story as well. This includes carrying out policy analysis and definition for Identity & Access management for 5G-connected IoT devices. The project will also employ a novel system architecture to construct the embedded computers that connect “things” to the network, enabling cryptographic proof of the trustworthiness of both IoT devices and servers in MECs and remote data centres.
Finally, let us consider the application layer and how all components cooperate. The light-green arrows in both figures visualise the major flow of information from the things layer through the various M2M platforms and the DVL to the applications at the top. These data flows are of course security critical, which is why all this data is anonymized and logged into the DLTs to ensure integrity, as well as to enable proof-of-existence of supply-chain records. However, these data flows do not require extremely low latency. In contrast, the light-blue arrows on the right side represent time-critical connections used to transmit sensor readings (e.g., camera feeds) and control commands to actuators (e.g., robot arms). Those connections also pass through the various network layers (not shown in the pictures. They are used for remote operation of robots and automated guided vehicles in the factory and drivers’ safety use cases, respectively. Here, short and bounded response times are of critical importance, which is also the reason why some computations for control operations might actually run Multi-access Edge Cloud (MEC) within the network.
The discussion and visualisations above show that the iNGENIOUS architecture is generic and applicable to many different use cases. Most of the components in the middle layers are shared and needed in all the supply-chain scenarios we consider. Differences only exist at the things layer and at the application level. This is of course expected, but there are similarities with regard to the DVL-supported data analytics techniques supporting the different use cases.
More details about the building blocks of the iNGENIOUS cross-layer architecture and the innovations enabled by them will be discussed in future articles on this blog.